Author: admin
Modify File Permissions with Linux chmod command (Ownership and Permissions)
Following are the symbolic representation of three different roles:
- u is for user
- g is for group
- o is for others
- a is for all
Following are the symbolic representation of three different permissions:
- r is for read permission
- w is for write permission
- x is for execute permission
This is called octal notation because the binary numbers are converted to base-8 by using the digits 0 to 7:
- 7, rwx, read, write, and execute
- 6, rw-, read and write
- 5, r-x, read and execute
- 4, r–, read only
- 3, -wx, write and execute
- 2, -w-, write only
- 1, –x, execute only
- 0, —, none
The format of a chmod command
chmod [who][+,-,=][permissions] filename
There are two ways to give permissions.
Here is the equivalent command using octal permissions notation.
chmod 754 file.txt
This example uses symbolic permissions notation.
chmod u=rwx,g=rx,o=r file.txt
a+x is same as +x
chmod -R +w,g=rw,o-rw, ~/group-project-files/
Copying permissions
The parameter g=u means grant group permissions to be same as the user’s.
chmod g=u ~/myFile.txt
Making a File Executable
chmod +x ~/group-project.py
Add single permission to a file/directory
chmod u+x filename
Add multiple permission to a file/directory
chmod u+r,g+x filename
Remove permission from a file/directory
chmod u-rx filename
Change permission for all roles on a file/directory
Following code assigns execute privilege to user, group and others (basically anybody can execute this file).
chmod a+x filename
Make permission for a file same as another file (using reference)
file2’s permission will be set exactly same as file1’s permission.
chmod –reference=file1 file2
Apply the permission to all the files under a directory recursively
chmod -R 755 directory-name/
Change execute permission only on the directories (files are not affected)
chmod u+X *
How To Use SSH to Connect to a Remote Server in Ubuntu
Enable SSH in Ubuntu Server
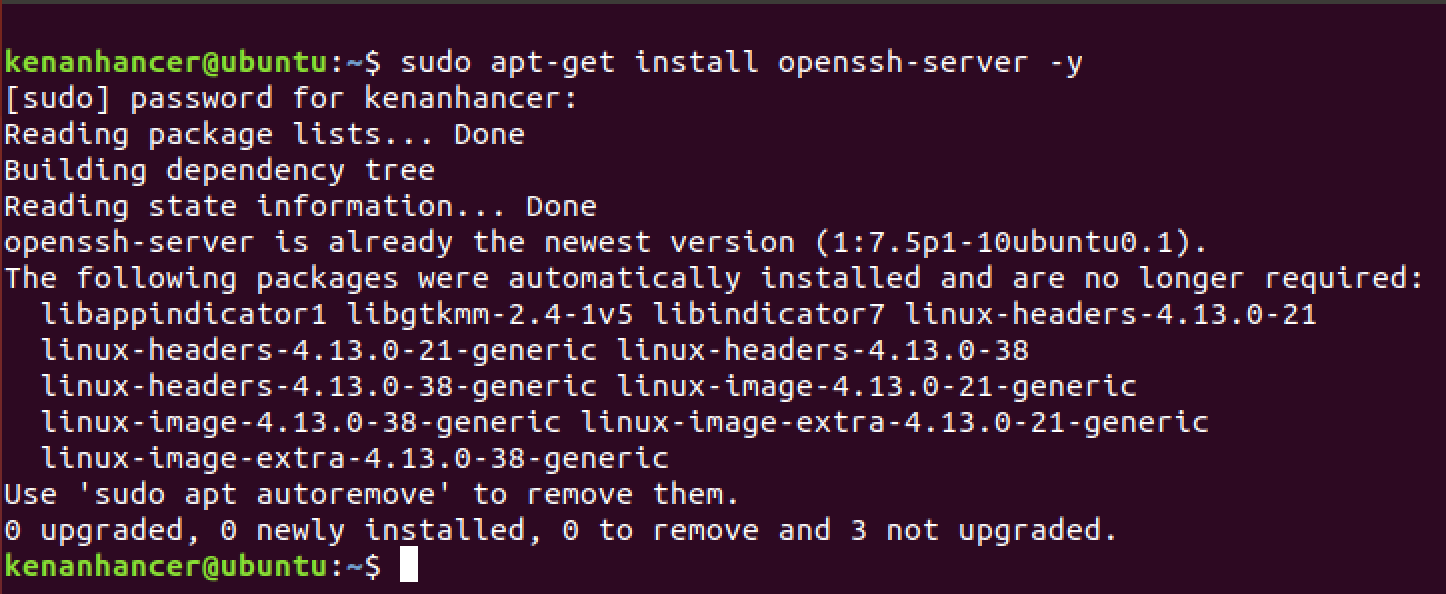
Install it by running the following command in your Ubuntu terminal.
sudo apt-get install openssh-server -y
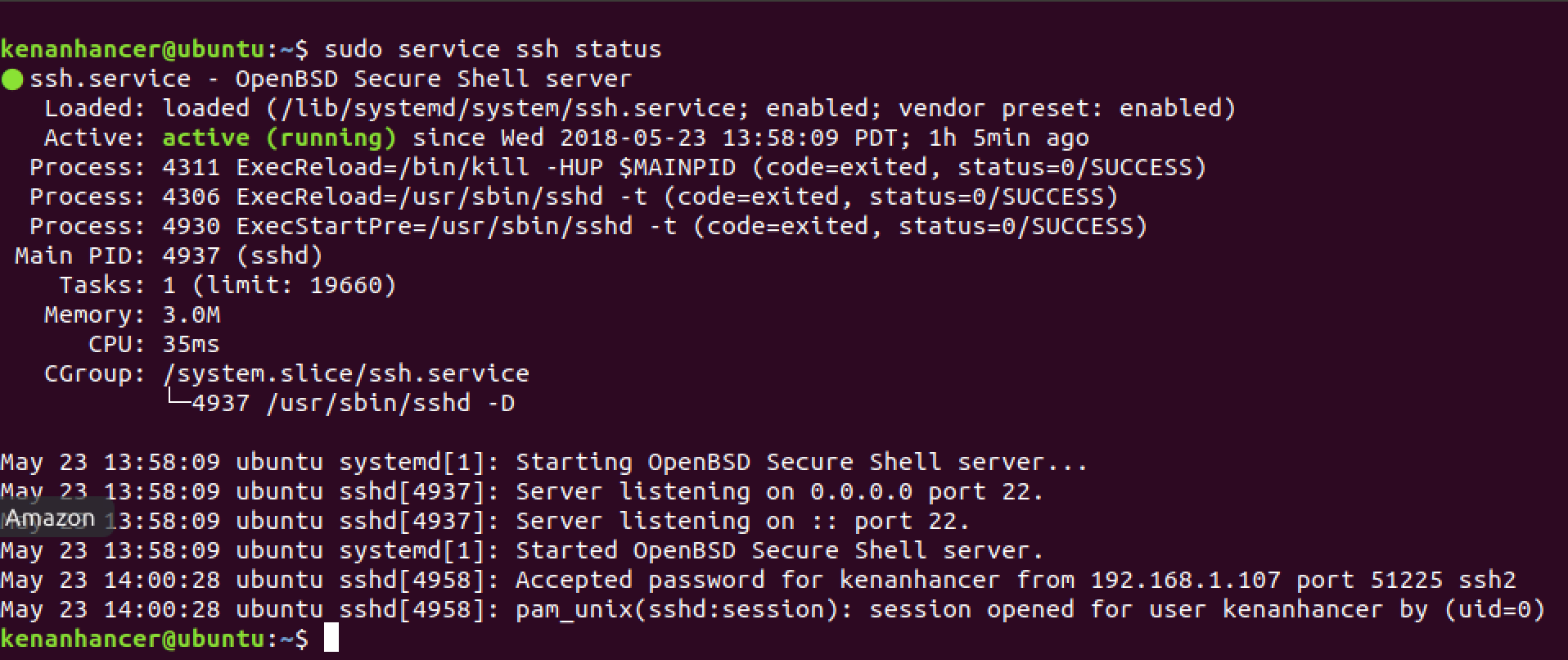
Check SSH Status
sudo service ssh status
Configure SSH in Ubuntu Server
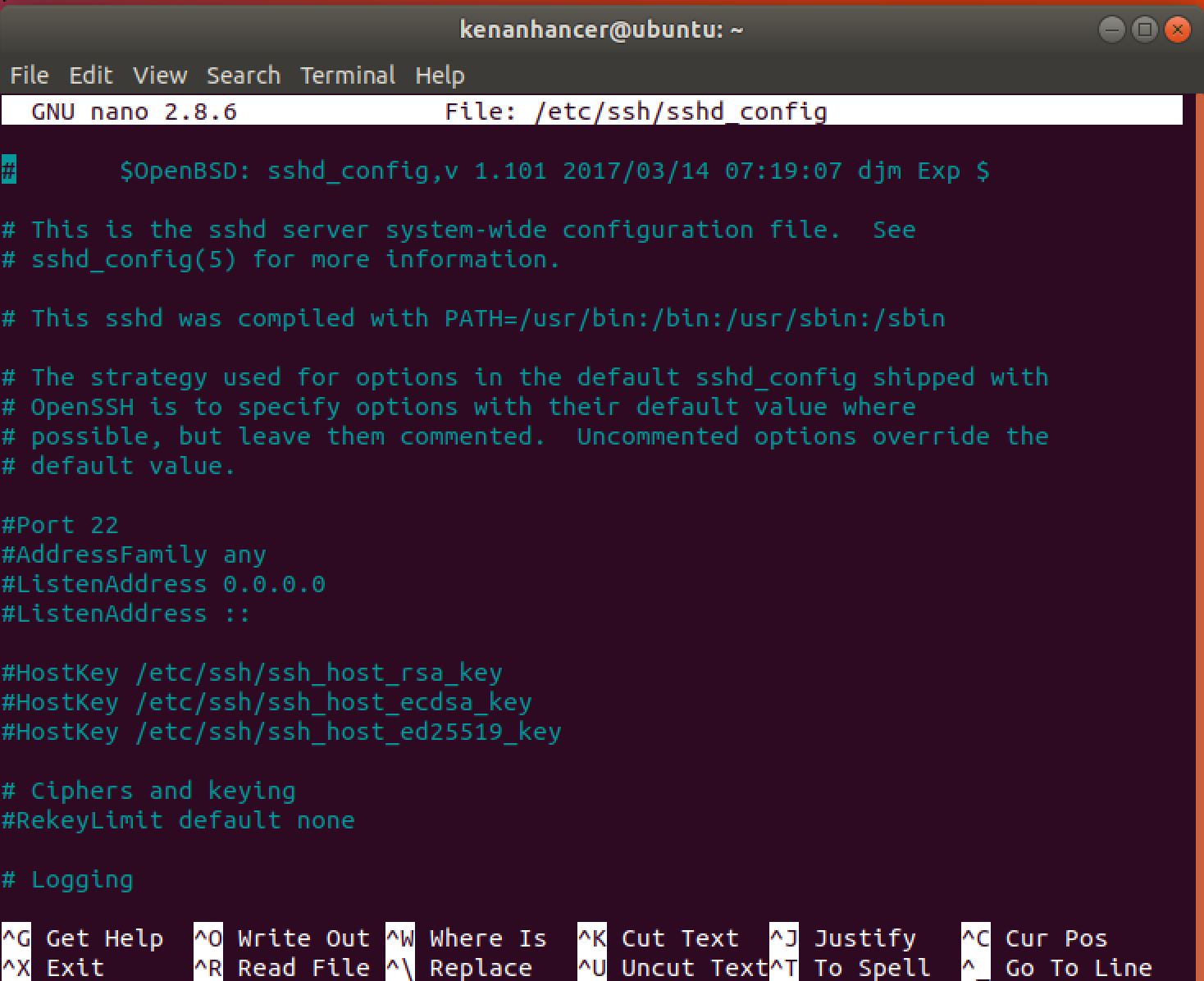
Configure SSH by running the following command in Ubuntu terminal.
sudo nano /etc/ssh/sshd_config
When you open the file, find and change the following item(default port)
# Port 22
to
Port 22
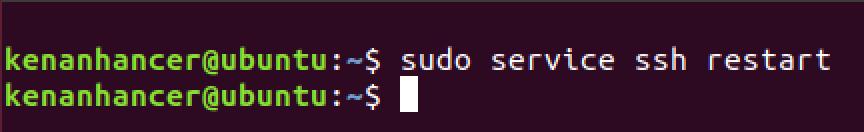
Restart SSH in Ubuntu Server
Apply the changes by restarting SSH.
sudo service ssh restart
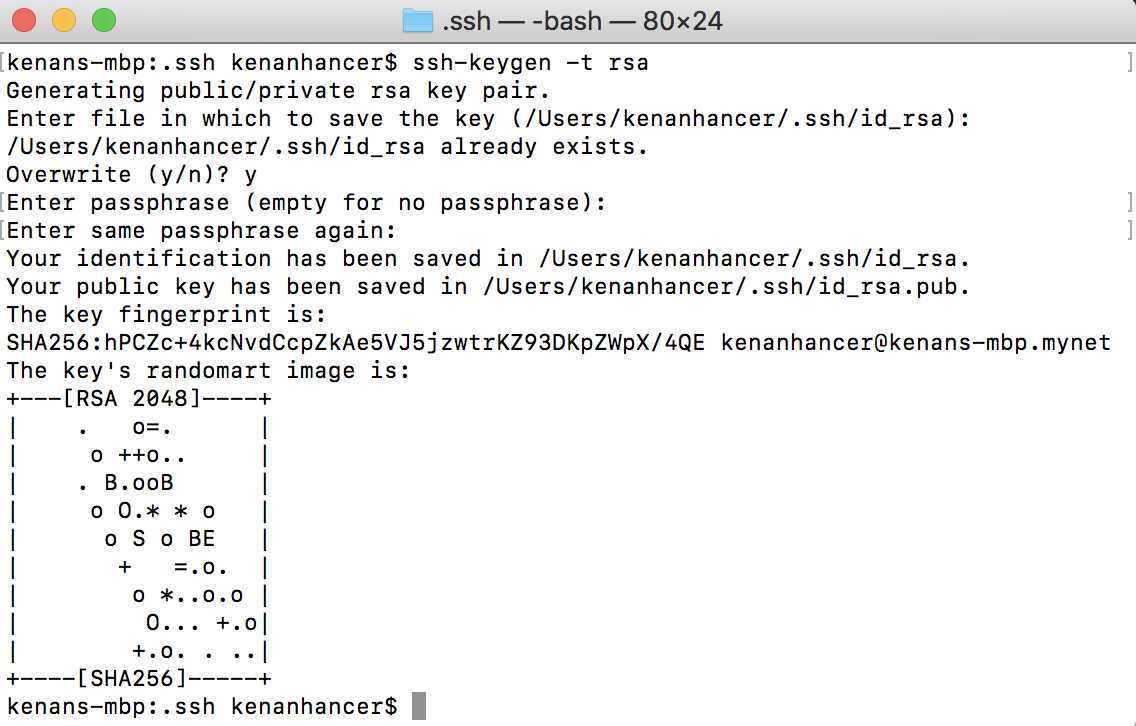
Create SSH Keys
SSH keys allow authentication between two hosts without the need of a password. SSH key authentication uses two keys, a private key and a public key. The first step is to create a key pair on the client machine
ssh-keygen -t rsa
Copy the public key to the remote server
There are 3 ways to copy your public key to remote server(Ubuntu etc.).
Copy public key using ssh-copy-id
To copy public key to remote computer run the following command in local computer.
ssh-copy-id username@remote_host
Copy public key using ssh
ssh kenanhancer
ssh kenanhancer@192.168.1.14
ssh username@remote_host -p port
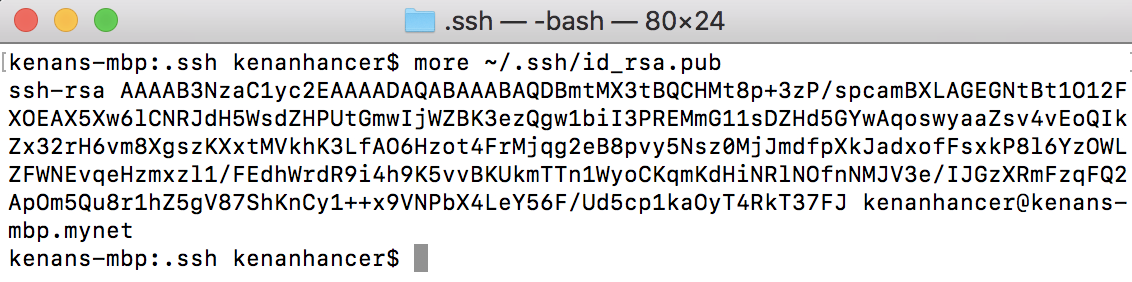
Copy public key manually
To display the content of your id_rsa.pub key, type this into your local computer.
cat ~/.ssh/id_rsa.pub
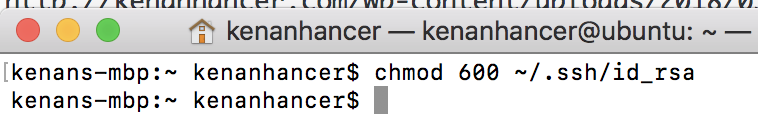
chmod 600 ~/.ssh/id_rsa
Connect to Remote computer
you should make sure the ~/.ssh directory exists. This command will create the directory if necessary, or do nothing if it already exists.
mkdir -p ~/.ssh
Copy public_key_string from local computer and paste instead of public_key_string in remote computer.
echo public_key_string >> ~/.ssh/authorized_keys
Example:
echo ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDBmtMX3tBQCHMt8p+3zP/spcamBXLAGEGNtBt1O12FXOEAX5Xw6lCNRJdH5WsdZHPUtGmwIjWZBK3ezQgw1biI3PREMmG11sDZHd5GYwAqoswyaaZsv4vEoQIkZx32rH6vm8XgszKXxtMVkhK3LfAO6Hzot4FrMjqg2eB8pvy5Nsz0MjJmdfpXkJadxofFsxkP8l6YzOWLZFWNEvqeHzmxzl1/FEdhWrdR9i4h9K5vvBKUkmTTn1WyoCKqmKdHiNRlNOfnNMJV3e/IJGzXRmFzqFQ2ApOm5Qu8r1hZ5gV87ShKnCy1++x9VNPbX4LeY56F/Ud5cp1kaOyT4RkT37FJ kenanhancer@kenans-mbp.mynet >> ~/.ssh/authorized_keys
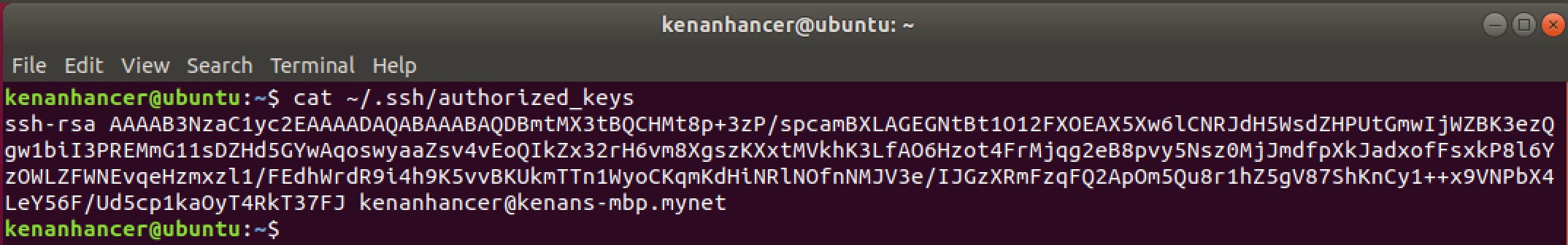
Check key in Remote computer if you want to see
cat ~/.ssh/authorized_keys
Login to Ubuntu Server via SSH
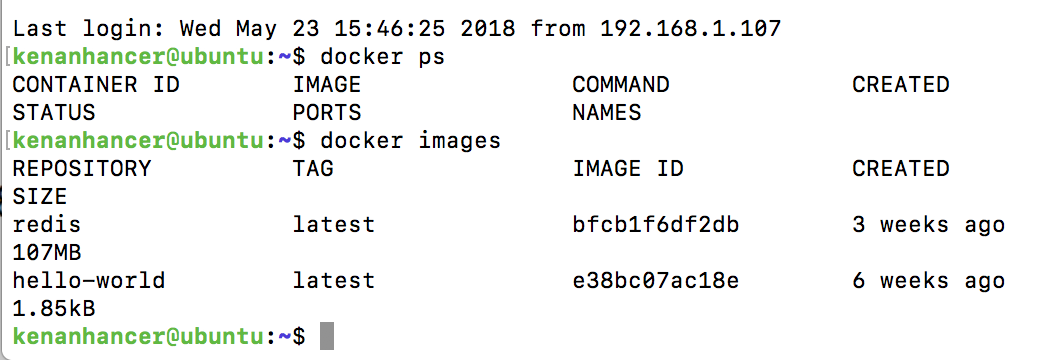
Let's check docker containers and docker images in remote Ubuntu server by running the following command from local computer
C# Repository Pattern Example 1
Id field can be declared as generic as shown in following sample code.
AngularJS Model, Controller
Gang of Four Patterns
Creational Patterns
Creational patterns are ones that create objects for you, rather than having you instantiate objects directly. This gives your program more flexibility in deciding which objects need to be created for a given case.
- Abstract factory: provide an interface for creating families of related or dependent objects without specifying their concrete classes.
- Builder: separate the construction of a complex object from its representation, allowing the same construction process to create various representations.
- Factory method: define an interface for creating a single object, but let subclasses decide which class to instantiate. Factory Method lets a class defer instantiation to subclasses.
- Prototype: specify the kinds of objects to create using a prototypical instance, and create new objects from the 'skeleton' of an existing object, thus boosting performance and keeping memory footprints to a minimum.
- Singleton: ensure a class has only one instance, and provide a global point of access to it.
Structural Patterns
These concern class and object composition. They use inheritance to compose interfaces and define ways to compose objects to obtain new functionality.
- Adapter: allows classes with incompatible interfaces to work together by wrapping its own interface around that of an already existing class.
- Bridge: decouples an abstraction from its implementation so that the two can vary independently.
- Composite: composes zero-or-more similar objects so that they can be manipulated as one object.
- Decorator: dynamically adds/overrides behaviour in an existing method of an object.
- Facade: provides a simplified interface to a large body of code.
- Flyweight: reduces the cost of creating and manipulating a large number of similar objects.
- Proxy: provides a placeholder for another object to control access, reduce cost, and reduce complexity.
Behavioral Patterns
Most of these design patterns are specifically concerned with communication between objects.
- Chain of responsibility: delegates commands to a chain of processing objects.
- Command: creates objects which encapsulate actions and parameters.
- Interpreter: implements a specialized language.
- Iterator: accesses the elements of an object sequentially without exposing its underlying representation.
- Mediator: allows loose coupling between classes by being the only class that has detailed knowledge of their methods.
- Memento: provides the ability to restore an object to its previous state (undo).
- Observer: is a publish/subscribe pattern which allows a number of observer objects to see an event.
- State: allows an object to alter its behavior when its internal state changes.
- Strategy: allows one of a family of algorithms to be selected on-the-fly at runtime.
- Template: method defines the skeleton of an algorithm as an abstract class, allowing its subclasses to provide concrete behavior.
- Visitor: separates an algorithm from an object structure by moving the hierarchy of methods into one object.