Enable SSH in Ubuntu Server
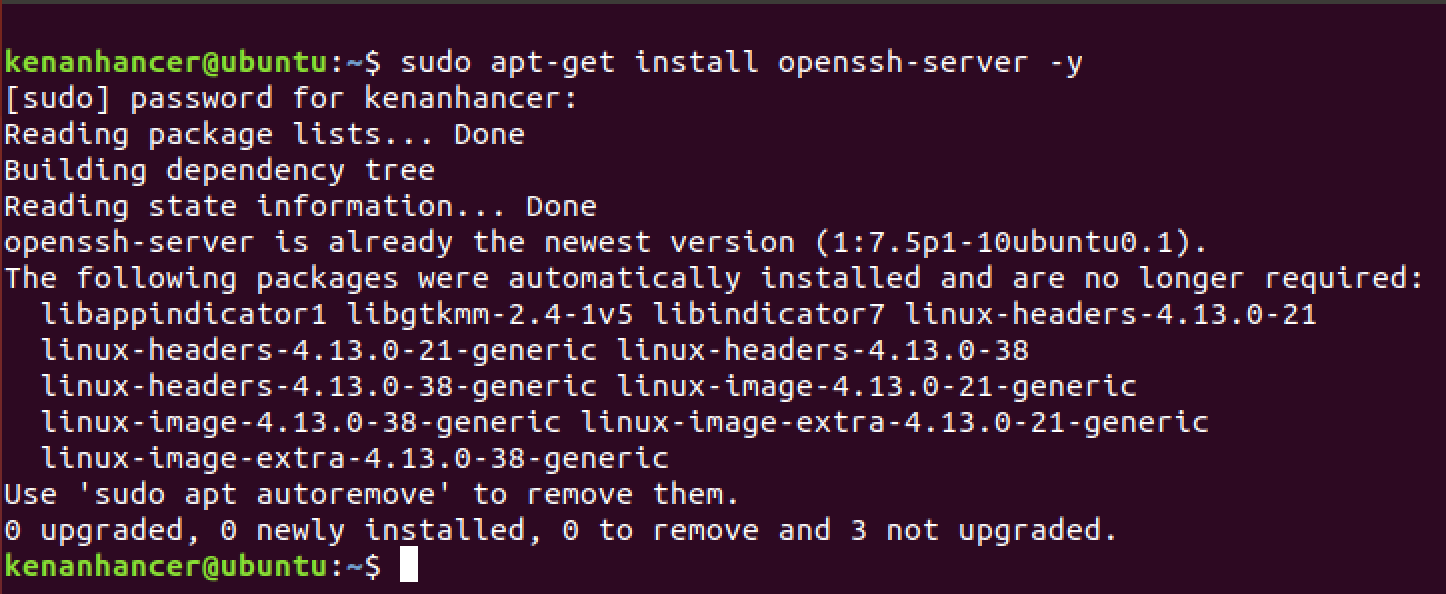
Install it by running the following command in your Ubuntu terminal.
sudo apt-get install openssh-server -y
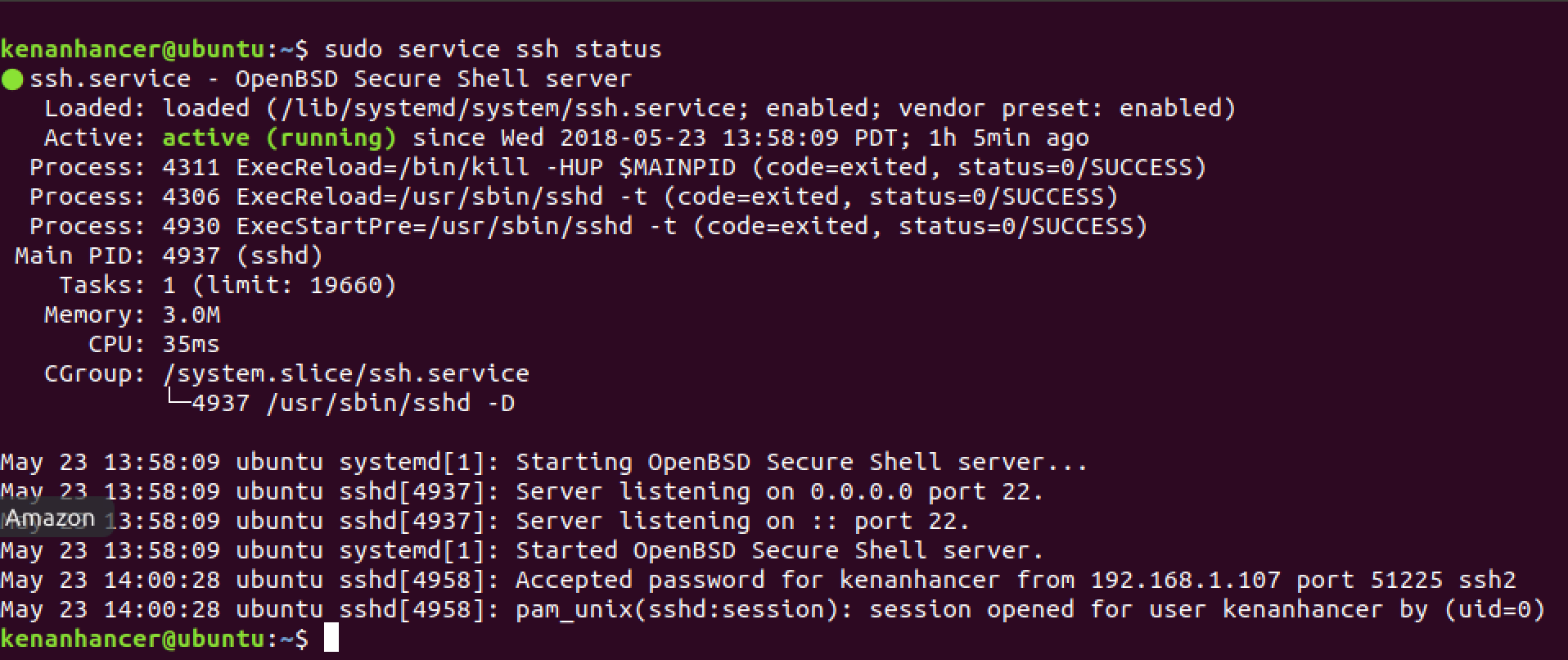
Check SSH Status
sudo service ssh status
Configure SSH in Ubuntu Server
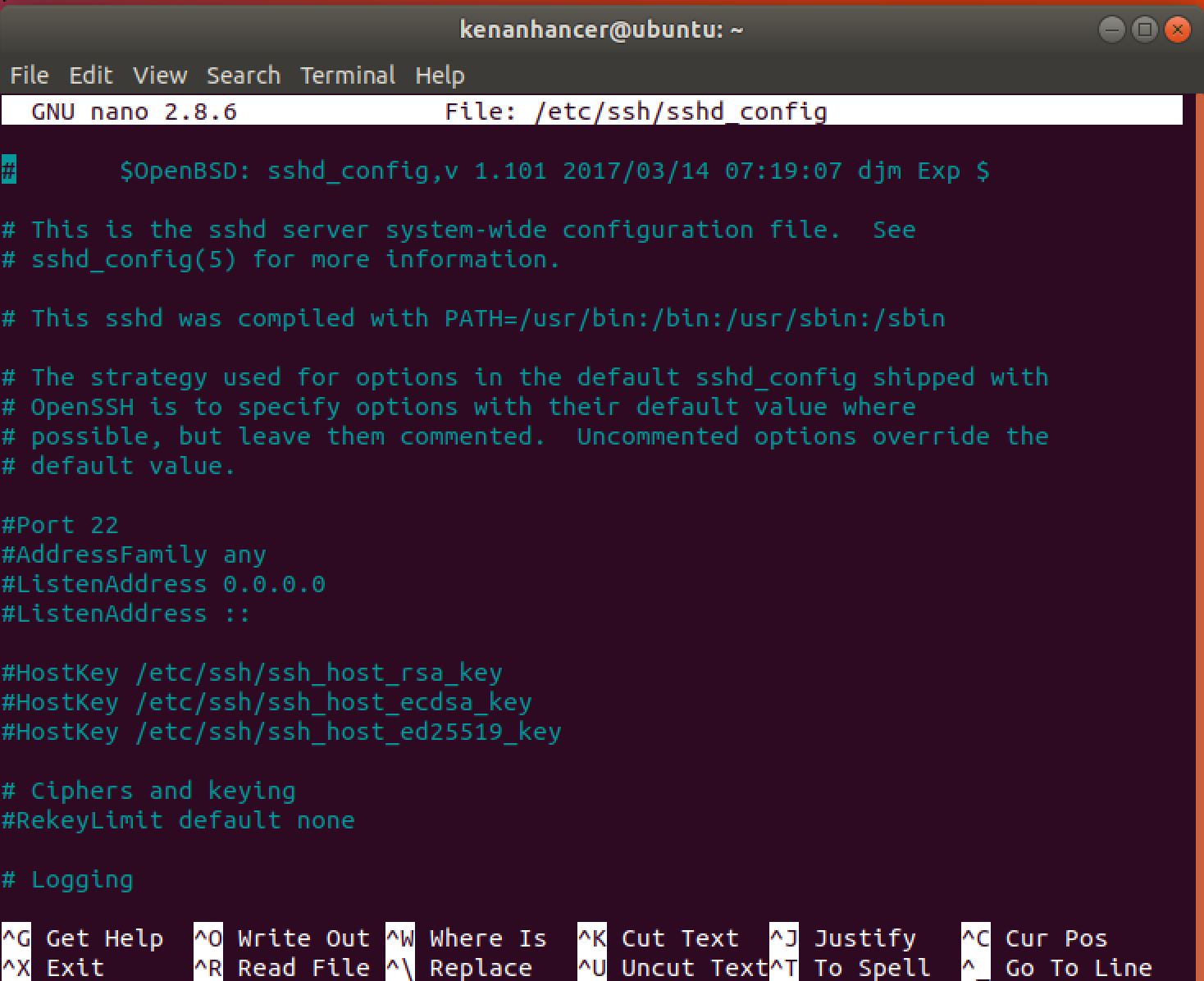
Configure SSH by running the following command in Ubuntu terminal.
sudo nano /etc/ssh/sshd_config
When you open the file, find and change the following item(default port)
# Port 22
to
Port 22
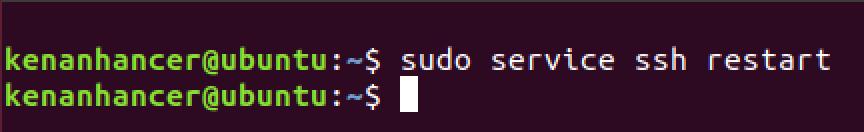
Restart SSH in Ubuntu Server
Apply the changes by restarting SSH.
sudo service ssh restart
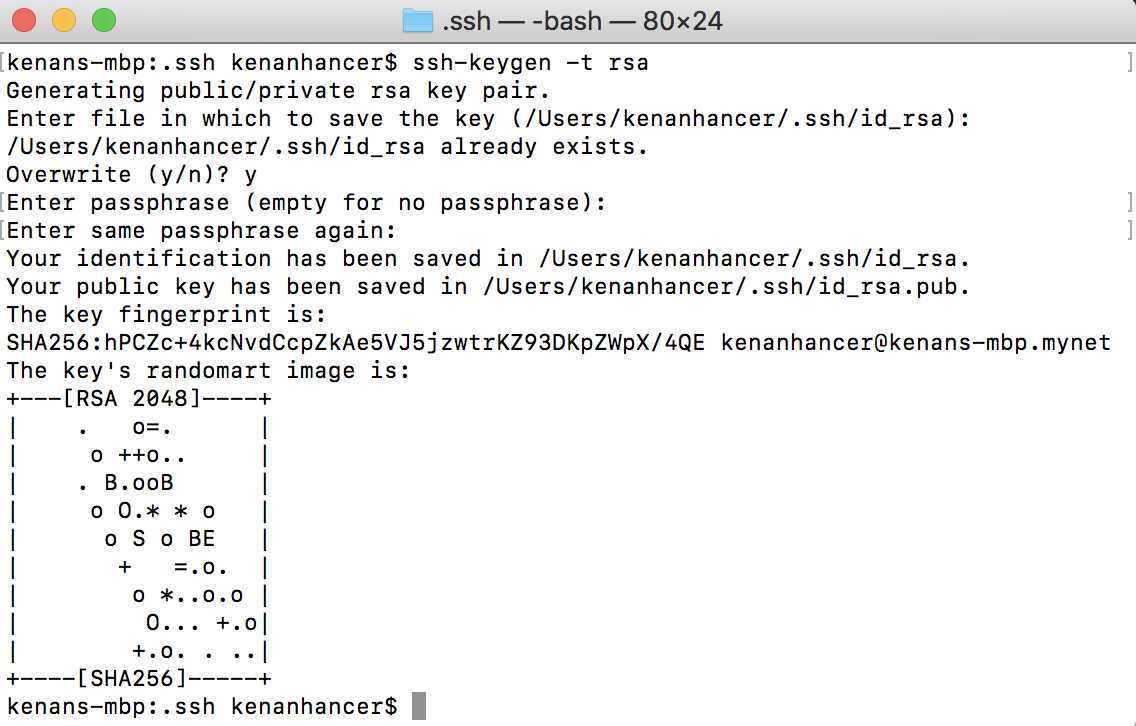
Create SSH Keys
SSH keys allow authentication between two hosts without the need of a password. SSH key authentication uses two keys, a private key and a public key. The first step is to create a key pair on the client machine
ssh-keygen -t rsa
Copy the public key to the remote server
There are 3 ways to copy your public key to remote server(Ubuntu etc.).
Copy public key using ssh-copy-id
To copy public key to remote computer run the following command in local computer.
ssh-copy-id username@remote_host
Copy public key using ssh
ssh kenanhancer
ssh kenanhancer@192.168.1.14
ssh username@remote_host -p port
Copy public key manually
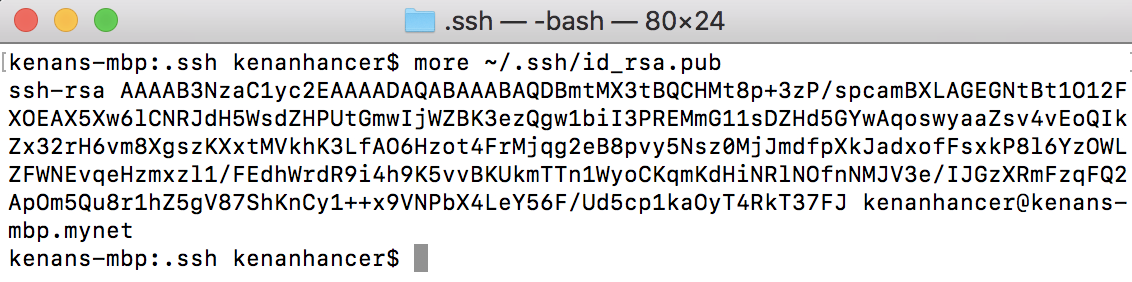
To display the content of your id_rsa.pub key, type this into your local computer.
cat ~/.ssh/id_rsa.pub
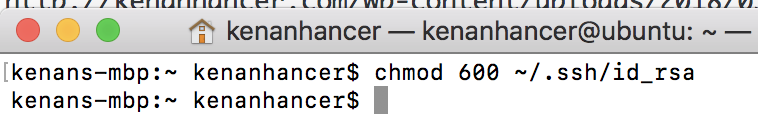
chmod 600 ~/.ssh/id_rsa
Connect to Remote computer
you should make sure the ~/.ssh directory exists. This command will create the directory if necessary, or do nothing if it already exists.
mkdir -p ~/.ssh
Copy public_key_string from local computer and paste instead of public_key_string in remote computer.
echo public_key_string >> ~/.ssh/authorized_keys
Example:
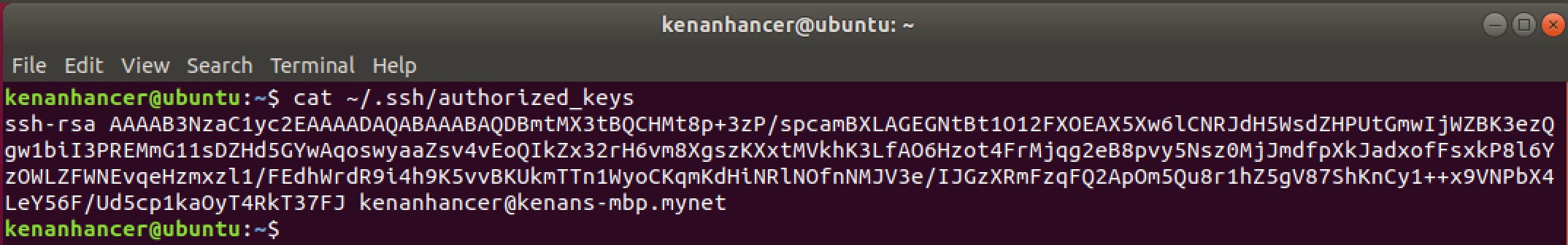
echo ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDBmtMX3tBQCHMt8p+3zP/spcamBXLAGEGNtBt1O12FXOEAX5Xw6lCNRJdH5WsdZHPUtGmwIjWZBK3ezQgw1biI3PREMmG11sDZHd5GYwAqoswyaaZsv4vEoQIkZx32rH6vm8XgszKXxtMVkhK3LfAO6Hzot4FrMjqg2eB8pvy5Nsz0MjJmdfpXkJadxofFsxkP8l6YzOWLZFWNEvqeHzmxzl1/FEdhWrdR9i4h9K5vvBKUkmTTn1WyoCKqmKdHiNRlNOfnNMJV3e/IJGzXRmFzqFQ2ApOm5Qu8r1hZ5gV87ShKnCy1++x9VNPbX4LeY56F/Ud5cp1kaOyT4RkT37FJ kenanhancer@kenans-mbp.mynet >> ~/.ssh/authorized_keys
Check key in Remote computer if you want to see
cat ~/.ssh/authorized_keys
Login to Ubuntu Server via SSH
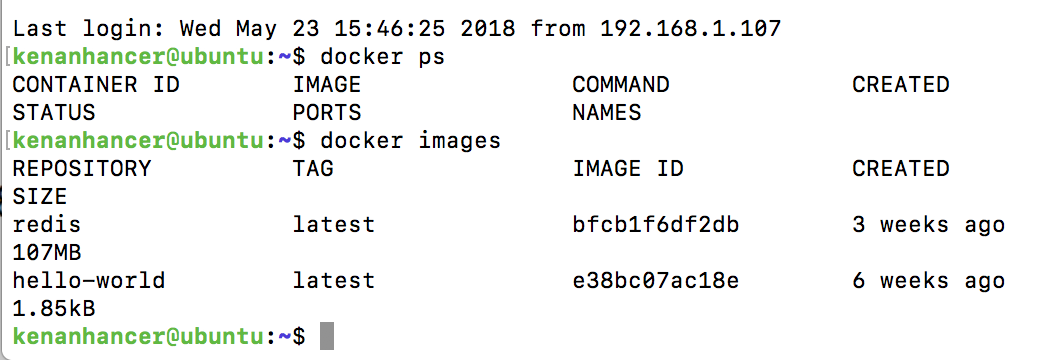
Let's check docker containers and docker images in remote Ubuntu server by running the following command from local computer